Home > Aplication >
Posted on 20 November 2010 by c0decstuff
Backward disassembler for ROP exploitation
bdasm is a PyCommand that I wrote for Immunity Debugger (v 1.73) which can search the address space of a process for a certain opcode/instruction and dissasemble backward and forward for a specified number of instructions.
This is especially useful in the exploit development process when existing gadget finding tools do not produce the results you need and you must extend your search manually.
When using the return-oriented-programming (ROP) technique for exploit development, you usually need to find useful instructions followed by RET. There are some tools to search for these gadgets (ex. pvefindaddr) but what if they do not find the gadgets you need? The search must be extended and bdasm is the tool you need.
Use case scenarios:
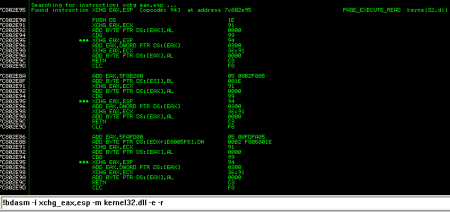
Example 1: Search for all occurences of instruction xchg eax,esp in the address space of module kernel32.dll and display the instructions before and after. Display results only if the page is executable (-e) and if the instructions after contain a RET (-r). The space character from an instruction must be replaced by _ :
!bdasm -i xchg_eax,esp -m kernel32.dll -e -r
Notes:
!bdasm -o 83c4 -m msvcrt.dll -e -r
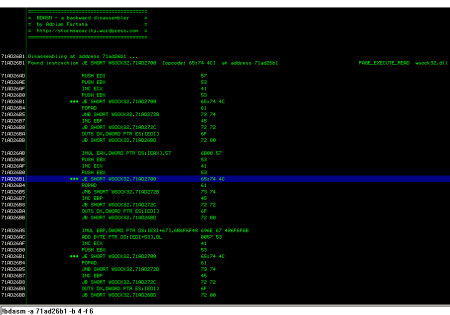
Example 3: Disassemble (backward and forward) from a specific address. Print maximum 4 instructions backward and 6 instructions forward:
!bdasm -a 71ad26b1 -b 4 -f 6
Installation and usage:
Copy bdasm.py into the PyCommands directory of your Immunity Debugger installation (my path is C:\Program Files\Immunity Inc\Immunity Debugger\PyCommands)
For usage instructions type: !bdasm in the Command Bar of Immunity Debugger.
bdasm is a PyCommand that I wrote for Immunity Debugger (v 1.73) which can search the address space of a process for a certain opcode/instruction and dissasemble backward and forward for a specified number of instructions.
This is especially useful in the exploit development process when existing gadget finding tools do not produce the results you need and you must extend your search manually.
When using the return-oriented-programming (ROP) technique for exploit development, you usually need to find useful instructions followed by RET. There are some tools to search for these gadgets (ex. pvefindaddr) but what if they do not find the gadgets you need? The search must be extended and bdasm is the tool you need.
Use case scenarios:
Example 1: Search for all occurences of instruction xchg eax,esp in the address space of module kernel32.dll and display the instructions before and after. Display results only if the page is executable (-e) and if the instructions after contain a RET (-r). The space character from an instruction must be replaced by _ :
!bdasm -i xchg_eax,esp -m kernel32.dll -e -r
Notes:
- As you can see in the screenshots, backward disassembling can produce multiple results from the same starting address because x86 instructions have variable lengths
- Backward disassembling does not always produce results when it is started from an arbitrary address because the previous bytes of that address do not always form a valid instruction
- bdasm tries to go backwards as many instructions as it can find, implementing a kind of backtracking algorithm
!bdasm -o 83c4 -m msvcrt.dll -e -r
Example 3: Disassemble (backward and forward) from a specific address. Print maximum 4 instructions backward and 6 instructions forward:
!bdasm -a 71ad26b1 -b 4 -f 6
Installation and usage:
Copy bdasm.py into the PyCommands directory of your Immunity Debugger installation (my path is C:\Program Files\Immunity Inc\Immunity Debugger\PyCommands)
For usage instructions type: !bdasm in the Command Bar of Immunity Debugger.
Category Article Aplication
Total Pageviews
Labels
- Android (1)
- Aplication (14)
- ARP (1)
- Backdoored (2)
- Browser (1)
- Cloud (1)
- Exploitation (1)
- Exploits (7)
- Facebook (2)
- forensics (3)
- Hacking (11)
- Hijacking (1)
- Honeypot (1)
- HTML5 (1)
- ios (2)
- Jailbreak (2)
- Linux (1)
- Malware (5)
- metasploit (2)
- Meterpreter (1)
- Movie (1)
- Networking (1)
- News (2)
- password attack (2)
- Penetration Test (2)
- Python (1)
- reverse engineering (1)
- Rootkits (1)
- Security (12)
- shellcode (2)
- Stuxnet/Duqu (2)
- Uncategories (1)
- Virus (1)
- Vulnerability (8)
- Web (5)
- Wifi (1)
- Windows (5)
Friendlist
Security Resources
-
-
-
This feed contains no entries
-
-
-
-
-
-
-
-
-